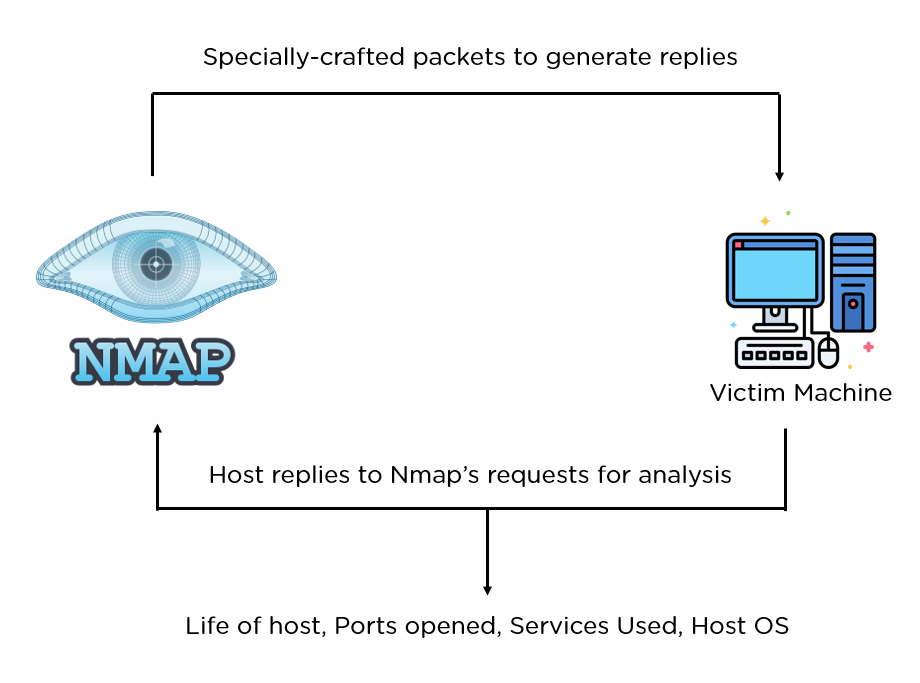
Nmap (Network Mapper) is a powerful and versatile open-source tool that is used for network discovery and security auditing. It was originally designed for security audits but can also be used for legitimate network discovery and diagnostic purposes.
Here’s a step-by-step guide on how to use Nmap for ethical hacking:
Installation: Nmap can be installed on Windows, macOS, and Linux systems. The installation process depends on the operating system you are using.
Scanning Basics: Nmap offers a variety of scan types, such as TCP SYN scans, TCP Connect scans, UDP scans, and others. Each scan type has its advantages and disadvantages. It’s essential to choose the right scan type based on your specific requirements and the network environment.
Target Specification: To scan a target network, you need to specify the target. You can use a hostname, IP address, IP address range, or CIDR notation to specify the target.
Port Scanning: Port scanning is the process of determining which ports on a target system are open and which are closed. Nmap offers several options to perform port scanning, such as service version detection (-sV), operating system detection (-O), and scanning specific port ranges (-p).
OS and Service Detection: Nmap can also identify the operating system and running services on the target system. This information can be valuable for security auditors to determine potential vulnerabilities.
Host Discovery: Nmap can be used to discover hosts that are up and running on the network. This is done using various host discovery techniques, such as ARP ping, ICMP ping, and others.
Nmap Scripting Engine (NSE): Nmap has a built-in scripting engine that allows users to write and execute custom scripts. The NSE comes with a wide range of pre-built scripts for various purposes, such as network vulnerability detection, configuration auditing, and others.
Here’s an example of a simple Nmap command:
Download
Copy code
nmap -p 80,443 target_hostname
In this example, Nmap scans the target system’s port 80 (HTTP) and port 443 (HTTPS).
It’s important to note that while Nmap can be used for legitimate network discovery and diagnostic purposes, its most common use is for security auditing. As a result, using Nmap without proper authorization or for malicious purposes is illegal and unethical. Always obtain permission from the network owner before scanning their network.
Additionally, remember that even the most advanced network scanning tools like Nmap can only detect certain vulnerabilities and security weaknesses. It’s essential to supplement network scanning with other ethical hacking techniques, such as penetration testing and vulnerability assessments, to fully understand and mitigate potential risks.
To summarize, Nmap is a powerful and versatile tool for ethical hacking, but it should only be used by authorized personnel for security auditing purposes. Always obtain permission from the network owner before scanning their network and use Nmap responsibly and ethically.
About Author
Discover more from SURFCLOUD TECHNOLOGY
Subscribe to get the latest posts sent to your email.