Securing an MS Access database involves implementing a number of security measures to protect your database from unauthorized access and damage. Here are some recommendations:
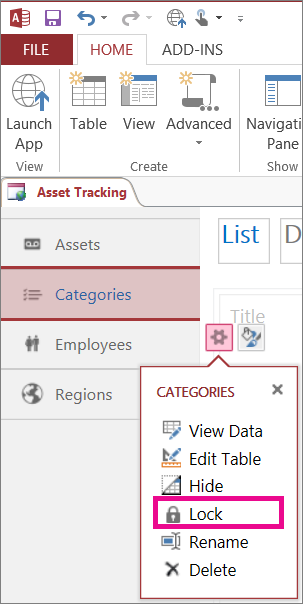
Set Database Permissions:
However, make sure the database can only be accessed by those who are allowed. In the MS Access user interface, you can set database permissions by right-clicking on the database and selecting “Properties.” Then, select the “Permissions” tab.
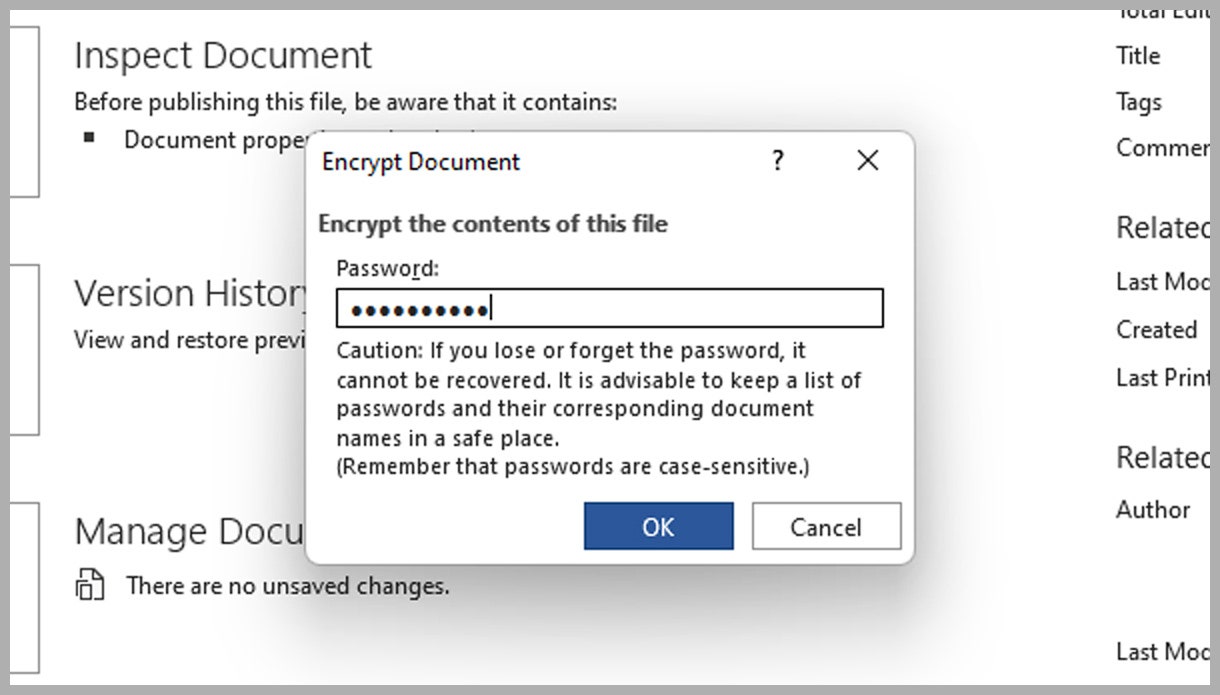
Enable database password protection
Set a strong password for your database. In the MS Access user interface, you can do this by right-clicking on the database and selecting “Password.” Then, select the “Yes” option under “Set database password” and enter a strong password.
Limit record-level data access
If possible, use table-level data access rather than record-level data access. This helps prevent users from accidentally modifying or deleting records.
Keep software up-to-date
Regularly update your MS Access software to ensure that you have the latest security patches.
Enable security warnings
Configure your MS Access settings to display security warnings. This helps alert you and your users to potential threats.
Limit data entry tasks
Minimize the number of tasks that users can perform on the database. This reduces the likelihood of errors or intentional damage.
Encrypt the database
Although MS Access does not have built-in encryption capabilities, you can use third-party tools to encrypt your database. This helps protect your data, even if it falls into the wrong hands.
By following these steps, you can significantly enhance the security of your MS Access database and minimize the risk of unauthorized access or damage.
About Author
Discover more from SURFCLOUD TECHNOLOGY
Subscribe to get the latest posts sent to your email.