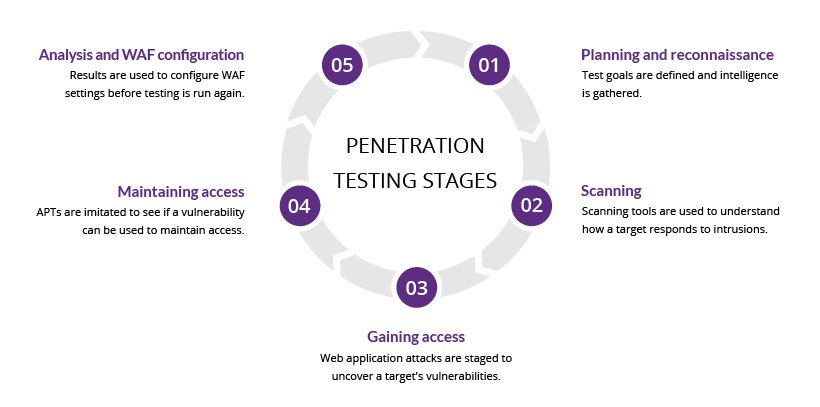
Penetration testing, also known as pen testing or ethical hacking, is the practice of simulating an attack on a computer system, network, or web application to identify vulnerabilities that could be exploited by a malicious actor. The goal of penetration testing is to identify and remediate vulnerabilities before they can be exploited by an attacker.
There are a number of different ways to perform penetration testing, but the most common approach is to use a combination of automated and manual techniques.
Automated tools can be used to scan for vulnerabilities in a system, while manual techniques can be used to exploit vulnerabilities that are found by the automated tools.
One of the most popular online penetration testing tools is Kali Linux, a Linux distribution that comes with a variety of pre-installed penetration testing tools.
Kali Linux can be used to perform a variety of penetration testing tasks, including scanning for vulnerabilities, exploiting vulnerabilities, and launching denial-of-service attacks.
Here are the steps on how to perform penetration testing online using Kali Linux:
1. Download and install Kali Linux on a virtual machine or a dedicated server.
2. Update the Kali Linux system.
3. Install the necessary penetration testing tools.
4. Scan the target system for vulnerabilities.
5. Exploit the vulnerabilities that are found.
6. Launch a denial-of-service attack.
7. Document the results of the penetration test.
It is important to note that penetration testing is a complex and challenging task, and it is important to have the necessary skills and knowledge before attempting to perform a penetration test. If you are not familiar with penetration testing, it is recommended that you consult with a qualified professional.
About Author
Discover more from SURFCLOUD TECHNOLOGY
Subscribe to get the latest posts sent to your email.