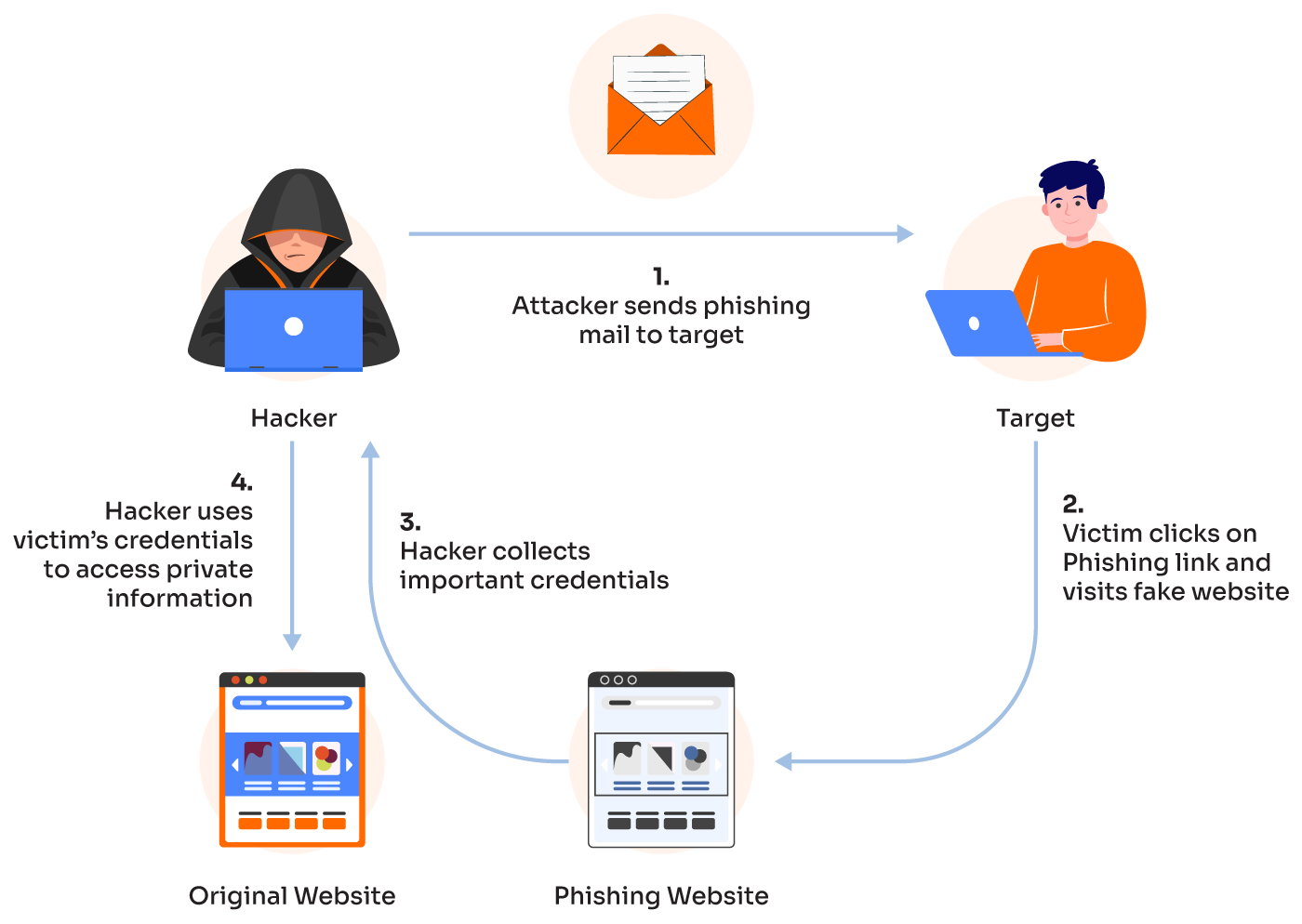
The aforementioned has lots of tactics to trick people into sharing their personal or sensitive information or downloading malware. Here are some of the common tactics they ascertained:
FAKE EMAILS
These are some of the emails that often appear to come from someone you know, or, in short, from reputable sources. Those sources are, for instance, banks, social media platforms, or even online stores. They end up asking you to open files such as attachments, fake customer numbers to be called, and even clicking on a website link looking to be legal and legitimate.
FAKE SMS/TEXT MEASSAGES (SMISHING)
This is also similar to phishing links and emails, scammers have a different way of sending text messages to users online, trying to track and get most of their details right after exploring the SMS content and thus replying to the message per whatever they asked. Most of these messages are often regarded as trusted ones from official companies.
FAKE WEBSITES
There are many websites that are designed to steal users private details online, leading to a greater proportion of what they need. However, sites that build demand for login credentials, financial information, or other sensitive data are very dangerous.
VISHING
This is also a type of phishing where scammers use their phones to call users and people nationwide, tricking or demanding that they provide information about themselves as they record everything during and/or after the call is placed. They normally post themselves as representatives of a legitimate organization and even encourage users to visit their websites, which is fake. With regards, all details are been collected by their cookies.
There are others known to be as follows:
- Scam Phone Calls
- Spear Phishing
- Whaling
- Clone Phishing
- Watering Hole Phishing
- Business Email Compromise (BEC)
About Author
Discover more from SURFCLOUD TECHNOLOGY
Subscribe to get the latest posts sent to your email.