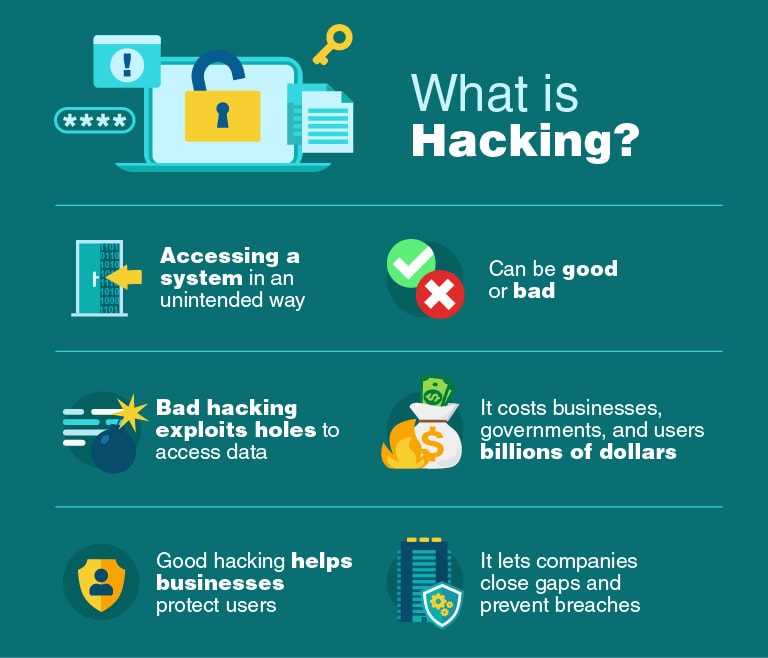
The process of exploring and getting into a main computer system, be it a network or other systems, is known as a penetration test. However, hacking turned out to be both authorized and unauthorized access to a computer system.
Metasploit Framework:
A comprehensive platform that offers an extensive database of exploits and auxiliary tools for ethical hacking and penetration testing. Metasploit can be utilized to discover, exploit, and validate vulnerabilities in various types of systems.
Wireshark:
An open-source network protocol analyzer that provides deep insights into the communication processes happening over a network Wireshark is an invaluable tool for identifying and fixing security loopholes, monitoring network usage, and analyzing the effectiveness of penetration testing techniques.
Nmap:
A powerful network scanning tool that can be used to discover hosts and services on a computer network by sending packets and analyzing the responses. Nmap is commonly used to conduct vulnerability scans, which involve identifying open ports, running version scans, and determining operating systems and services in use.
Burp Suite:
An integrated platform for conducting advanced penetration testing, vulnerability discovery, and security auditing of web applications Burp Suite provides various features, such as an interactive scanner, an intruder, a repeater, and a comprehensive set of utilities to aid in security testing.
John the Ripper:
A widely-used password-cracking tool that can be employed to test the strength of password systems John the Ripper is capable of cracking a wide variety of password hashes and supports several different cracking modes, such as brute force, dictionary attacks, and rules-based attacks.
Kali Linux:
A popular open-source penetration testing and security auditing platform based on Debian Kali Linux includes numerous pre-installed tools and utilities, such as Metasploit, Wireshark, Nmap, and Burp Suite, which can be used to conduct a wide range of security assessments and penetration tests.
OWASP Zed Attack Proxy (ZAP):
An open-source web application security tool that helps identify vulnerabilities in web applications during the development and testing phases ZAP can be used to intercept, manipulate, and debug HTTP and HTTPS requests and responses, providing developers with an opportunity to fix security flaws before deploying applications into production.
OpenVAS:
An open-source vulnerability scanning and management solution that integrates the Nessus and OpenVAS projects OpenVAS provides a comprehensive framework for vulnerability detection, allowing users to discover, assess, and report on the security posture of their IT infrastructure.
About Author
Discover more from SURFCLOUD TECHNOLOGY
Subscribe to get the latest posts sent to your email.